Compare commits
103 Commits
| Author | SHA1 | Date |
|---|---|---|
|
|
bd0c7c94b5 | |
|
|
d70e4c2974 | |
|
|
4e29fb5a21 | |
|
|
0f2edb1a71 | |
|
|
8ac2539a2a | |
|
|
97f4d5f2bc | |
|
|
9b7b09ada3 | |
|
|
c94811e63d | |
|
|
3e67047c73 | |
|
|
ecee75716e | |
|
|
fb6933dc64 | |
|
|
dc6921a1ac | |
|
|
3167762cfd | |
|
|
44223c5308 | |
|
|
dbe208fc48 | |
|
|
aca4e2a9b1 | |
|
|
c1c1ac4dbb | |
|
|
ba0daa6769 | |
|
|
227c0aab1e | |
|
|
8ba3751cf7 | |
|
|
d013c0a7d2 | |
|
|
cbe8ba10ce | |
|
|
9c2587bca5 | |
|
|
2a5ddc87bf | |
|
|
2ef6c1c80e | |
|
|
3c224018f4 | |
|
|
b8f8c81d51 | |
|
|
f34dd5fa7b | |
|
|
c0869d7341 | |
|
|
e99a548dcc | |
|
|
3d475dfaec | |
|
|
cba5010c2a | |
|
|
c5661f098f | |
|
|
6844c01242 | |
|
|
0811f28ac6 | |
|
|
9bb79a18eb | |
|
|
0d93c6ffb4 | |
|
|
6a61df200e | |
|
|
e4b313fe79 | |
|
|
a2843575be | |
|
|
60c71ccb7a | |
|
|
48abeb5950 | |
|
|
3c988cc73a | |
|
|
bea5cfc3b8 | |
|
|
b68ebe67f2 | |
|
|
a6c943d38f | |
|
|
dd162301ff | |
|
|
5f6471d9a4 | |
|
|
2a5b965b98 | |
|
|
ee266d43b7 | |
|
|
b61baa90df | |
|
|
a98d92f8bc | |
|
|
b7c8c4115a | |
|
|
4e7c52767d | |
|
|
8473d9ba6b | |
|
|
0af4830224 | |
|
|
81a4329d71 | |
|
|
3679776f3c | |
|
|
ba131fcd2f | |
|
|
ae6bc31c2c | |
|
|
6d7a6b3666 | |
|
|
16f2160be5 | |
|
|
7cad9301b3 | |
|
|
580549812a | |
|
|
a485c7882a | |
|
|
7d13f7a0ef | |
|
|
226b2375ab | |
|
|
052a3e66d1 | |
|
|
05d862709d | |
|
|
3846913899 | |
|
|
a87ace1f98 | |
|
|
0ba71a443e | |
|
|
3a486e9985 | |
|
|
23564cda5d | |
|
|
0ea21d09bd | |
|
|
08e30e156d | |
|
|
6d35e780f4 | |
|
|
4ec3154be0 | |
|
|
843f26630d | |
|
|
7fc2ec65b9 | |
|
|
c8cdfd54da | |
|
|
f0c33c7a32 | |
|
|
9e874397da | |
|
|
76cb73f3cb | |
|
|
90f23d286e | |
|
|
e41e311a7f | |
|
|
1f75f01630 | |
|
|
14a53b19da | |
|
|
d8f0ddd7a5 | |
|
|
62d3448a54 | |
|
|
cb6d139629 | |
|
|
7e2db09ed9 | |
|
|
33cf1cde79 | |
|
|
4a3006e196 | |
|
|
36f98eff95 | |
|
|
fa7b8f9567 | |
|
|
3beefc2587 | |
|
|
27c36fdb80 | |
|
|
3d21dae168 | |
|
|
7d2a510146 | |
|
|
a1a35c9b35 | |
|
|
eec77e1ab9 | |
|
|
5633d374de |
|
|
@ -1,6 +1,6 @@
|
|||
name: CI
|
||||
|
||||
on: [push]
|
||||
on: [push, pull_request]
|
||||
|
||||
jobs:
|
||||
build:
|
||||
|
|
@ -10,7 +10,7 @@ jobs:
|
|||
steps:
|
||||
- uses: actions/checkout@v1
|
||||
- name: install prerequisites
|
||||
run: sudo apt-get install -y shellcheck jq
|
||||
run: sudo apt-get update && sudo apt-get install -y shellcheck jq sqlite3 iucode-tool
|
||||
- name: shellcheck
|
||||
run: shellcheck -s sh spectre-meltdown-checker.sh
|
||||
- name: check indentation
|
||||
|
|
@ -24,7 +24,7 @@ jobs:
|
|||
fi
|
||||
- name: check direct execution
|
||||
run: |
|
||||
expected=14
|
||||
expected=19
|
||||
nb=$(sudo ./spectre-meltdown-checker.sh --batch json | jq '.[]|.CVE' | wc -l)
|
||||
if [ "$nb" -ne "$expected" ]; then
|
||||
echo "Invalid number of CVEs reported: $nb instead of $expected"
|
||||
|
|
@ -34,7 +34,7 @@ jobs:
|
|||
fi
|
||||
- name: check docker-compose run execution
|
||||
run: |
|
||||
expected=14
|
||||
expected=19
|
||||
docker-compose build
|
||||
nb=$(docker-compose run --rm spectre-meltdown-checker --batch json | jq '.[]|.CVE' | wc -l)
|
||||
if [ "$nb" -ne "$expected" ]; then
|
||||
|
|
@ -45,7 +45,7 @@ jobs:
|
|||
fi
|
||||
- name: check docker run execution
|
||||
run: |
|
||||
expected=14
|
||||
expected=19
|
||||
docker build -t spectre-meltdown-checker .
|
||||
nb=$(docker run --rm --privileged -v /boot:/boot:ro -v /dev/cpu:/dev/cpu:ro -v /lib/modules:/lib/modules:ro spectre-meltdown-checker --batch json | jq '.[]|.CVE' | wc -l)
|
||||
if [ "$nb" -ne "$expected" ]; then
|
||||
|
|
@ -54,3 +54,20 @@ jobs:
|
|||
else
|
||||
echo "OK $nb CVEs reported"
|
||||
fi
|
||||
- name: check fwdb update
|
||||
run: |
|
||||
nbtmp1=$(find /tmp 2>/dev/null | wc -l)
|
||||
./spectre-meltdown-checker.sh --update-fwdb; ret=$?
|
||||
if [ "$ret" != 0 ]; then
|
||||
echo "Non-zero return value: $ret"
|
||||
exit 1
|
||||
fi
|
||||
nbtmp2=$(find /tmp 2>/dev/null | wc -l)
|
||||
if [ "$nbtmp1" != "$nbtmp2" ]; then
|
||||
echo "Left temporary files!"
|
||||
exit 1
|
||||
fi
|
||||
if ! [ -e ~/.mcedb ]; then
|
||||
echo "No .mcedb file found after updating fwdb"
|
||||
exit 1
|
||||
fi
|
||||
|
|
|
|||
|
|
@ -1,7 +1,7 @@
|
|||
FROM alpine:3.7
|
||||
FROM alpine:latest
|
||||
|
||||
RUN apk --update --no-cache add kmod binutils grep perl
|
||||
RUN apk --update --no-cache add kmod binutils grep perl zstd wget sharutils unzip sqlite procps coreutils iucode-tool gzip xz bzip2 lz4
|
||||
|
||||
COPY . /check
|
||||
COPY spectre-meltdown-checker.sh /
|
||||
|
||||
ENTRYPOINT ["/check/spectre-meltdown-checker.sh"]
|
||||
ENTRYPOINT ["/spectre-meltdown-checker.sh"]
|
||||
|
|
|
|||
|
|
@ -0,0 +1,145 @@
|
|||
# Questions
|
||||
|
||||
- [What to expect from this tool?](#what-to-expect-from-this-tool)
|
||||
- [Why was this script written in the first place?](#why-was-this-script-written-in-the-first-place)
|
||||
- [Why are those vulnerabilities so different than regular CVEs?](#why-are-those-vulnerabilities-so-different-than-regular-cves)
|
||||
- [What do "affected", "vulnerable" and "mitigated" mean exactly?](#what-do-affected-vulnerable-and-mitigated-mean-exactly)
|
||||
- [What are the main design decisions regarding this script?](#what-are-the-main-design-decisions-regarding-this-script)
|
||||
- [Everything is indicated in `sysfs` now, is this script still useful?](#everything-is-indicated-in-sysfs-now-is-this-script-still-useful)
|
||||
- [How does this script work?](#how-does-this-script-work)
|
||||
- [Which BSD OSes are supported?](#which-bsd-oses-are-supported)
|
||||
- [Why is my OS not supported?](#why-is-my-os-not-supported)
|
||||
- [The tool says there is an updated microcode for my CPU, but I don't have it!](#the-tool-says-there-is-an-updated-microcode-for-my-cpu-but-i-dont-have-it)
|
||||
- [The tool says that I need a more up-to-date microcode, but I have the more recent version!](#the-tool-says-that-i-need-a-more-up-to-date-microcode-but-i-have-the-more-recent-version)
|
||||
- [Which rules are governing the support of a CVE in this tool?](#which-rules-are-governing-the-support-of-a-cve-in-this-tool)
|
||||
|
||||
# Answers
|
||||
|
||||
## What to expect from this tool?
|
||||
|
||||
This tool does its best to determine where your system stands on each of the collectively named [transient execution](https://en.wikipedia.org/wiki/Transient_execution_CPU_vulnerability) vulnerabilities (also sometimes called "speculative execution" vulnerabilities) that were made public since early 2018. It doesn't attempt to run any kind of exploit, and can't guarantee that your system is secure, but rather helps you verifying if your system is affected, and if it is, checks whether it has the known mitigations in place to avoid being vulnerable.
|
||||
Some mitigations could also exist in your kernel that this script doesn't know (yet) how to detect, or it might falsely detect mitigations that in the end don't work as expected (for example, on backported or modified kernels).
|
||||
|
||||
Please also note that for Spectre vulnerabilities, all software can possibly be exploited, this tool only verifies that the kernel (which is the core of the system) you're using has the proper protections in place. Verifying all the other software is out of the scope of this tool. As a general measure, ensure you always have the most up to date stable versions of all the software you use, especially for those who are exposed to the world, such as network daemons and browsers.
|
||||
|
||||
This tool has been released in the hope that it'll be useful, but don't use it to jump to definitive conclusions about your security: hardware vulnerabilities are [complex beasts](#why-are-those-vulnerabilities-so-different-than-regular-cves), and collective understanding of each vulnerability is evolving with time.
|
||||
|
||||
## Why was this script written in the first place?
|
||||
|
||||
The first commit of this script is dated *2018-01-07*, only 4 days after the world first heard about the Meltdown and the Spectre attacks. With those attacks disclosure, a _whole new range of vulnerabilities_ that were previously thought to be mostly theoretical and only possible in very controlled environments (labs) - hence of little interest for most except researchers - suddenly became completely mainstream and apparently trivial to conduct on an immensely large number of systems.
|
||||
|
||||
On the few hours and days after that date, the whole industry went crazy. Proper, verified information about these vulnerabilities was incredibly hard to find, because before this, even the CPU vendors never had to deal with managing security vulnerabilities at scale, as software vendors do since decades. There were a lot of FUD, and the apparent silence of the vendors was enough for most to fear the worst. The whole industry had everything to learn about this new type of vulnerabilities. However, most systems administrators had a few simple questions:
|
||||
|
||||
- Am **I** vulnerable? And if yes,
|
||||
- What do I have to do to mitigate these vulnerabilities on **my** system?
|
||||
|
||||
Unfortunately, answering those questions was very difficult (and still is to some extent), even if the safe answer to the first question was "you probably are". This script was written to try to give simple answers to those simple questions, and was made to evolve as the information about these vulnerabilities became available. On the first few days, there was several new versions published **per day**.
|
||||
|
||||
## Why are those vulnerabilities so different than regular CVEs?
|
||||
|
||||
Those are hardware vulnerabilities, while most of the CVEs we see everyday are software vulnerabilities. A quick comparison would be:
|
||||
|
||||
Software vulnerability:
|
||||
- Can be fixed? Yes.
|
||||
- How to fix? Update the software (or uninstall it!)
|
||||
|
||||
Hardware vulnerability:
|
||||
- Can be fixed? No, only mitigated (or buy new hardware!)
|
||||
- How to ~~fix~~ mitigate? In the worst case scenario, 5 "layers" need to be updated: the microcode/firmware, the host OS kernel, the hypervisor, the VM OS kernel, and possibly all the software running on the machine. Sometimes only a subset of those layers need to be updated. In yet other cases, there can be several possible mitigations for the same vulnerability, implying different layers. Yes, it can get horribly complicated.
|
||||
|
||||
A more detailed video explanation is available here: https://youtu.be/2gB9U1EcCss?t=425
|
||||
|
||||
## What do "affected", "vulnerable" and "mitigated" mean exactly?
|
||||
|
||||
- **Affected** means that your CPU's hardware, as it went out of the factory, is known to be concerned by a specific vulnerability, i.e. the vulnerability applies to your hardware model. Note that it says nothing about whether a given vulnerability can actually be used to exploit your system. However, an unaffected CPU will never be vulnerable, and doesn't need to have mitigations in place.
|
||||
- **Vulnerable** implies that you're using an **affected** CPU, and means that a given vulnerability can be exploited on your system, because no (or insufficient) mitigations are in place.
|
||||
- **Mitigated** implies that a previously **vulnerable** system has followed all the steps (updated all the required layers) to ensure a given vulnerability cannot be exploited. About what "layers" mean, see [the previous question](#why-are-those-vulnerabilities-so-different-than-regular-cves).
|
||||
|
||||
## What are the main design decisions regarding this script?
|
||||
|
||||
There are a few rules that govern how this tool is written.
|
||||
|
||||
1) It should be okay to run this script in a production environment. This implies, but is not limited to:
|
||||
|
||||
* 1a. Never modify the system it's running on, and if it needs to e.g. load a kernel module it requires, that wasn't loaded before it was launched, it'll take care to unload it on exit
|
||||
* 1b. Never attempt to "fix" or "mitigate" any vulnerability, or modify any configuration. It just reports what it thinks is the status of your system. It leaves all decisions to the sysadmin.
|
||||
* 1c. Never attempt to run any kind of exploit to tell whether a vulnerability is mitigated, because it would violate 1a), could lead to unpredictable system behavior, and might even lead to wrong conclusions, as some PoC must be compiled with specific options and prerequisites, otherwise giving wrong information (especially for Spectre). If you want to run PoCs, do it yourself, but please read carefully about the PoC and the vulnerability. PoCs about a hardware vulnerability are way more complicated and prone to false conclusions than PoCs for software vulnerabilities.
|
||||
|
||||
2) Never look at the kernel version to tell whether it supports mitigation for a given vulnerability. This implies never hardcoding version numbers in the script. This would defeat the purpose: this script should be able to detect mitigations in unknown kernels, with possibly backported or forward-ported patches. Also, don't believe what `sysfs` says, when possible. See the next question about this.
|
||||
|
||||
3) Never look at the microcode version to tell whether it has the proper mechanisms in place to support mitigation for a given vulnerability. This implies never hardcoding version numbers in the script. Instead, look for said mechanisms, as the kernel would do.
|
||||
|
||||
4) When a CPU is not known to be explicitly unaffected by a vulnerability, make the assumption that it is. This strong design choice has it roots in the early speculative execution vulnerability days (see [this answer](#why-was-this-script-written-in-the-first-place)), and is still a good approach as of today.
|
||||
|
||||
## Everything is indicated in `sysfs` now, is this script still useful?
|
||||
|
||||
A lot as changed since 2018. Nowadays, the industry adapted and this range of vulnerabilities is almost "business as usual", as software vulnerabilities are. However, due to their complexity, it's still not as easy as just checking a version number to ensure a vulnerability is closed.
|
||||
|
||||
Granted, we now have a standard way under Linux to check whether our system is affected, vulnerable, mitigated against most of these vulnerabilities. By having a look at the `sysfs` hierarchy, and more precisely the `/sys/devices/system/cpu/vulnerabilities/` folder, one can have a pretty good insight about its system state for each of the listed vulnerabilities. Note that the output can be a little different with some vendors (e.g. Red Hat has some slightly different output than the vanilla kernel for some vulnerabilities), but it's still a gigantic leap forward, given where we were in 2018 when this script was started, and it's very good news. The kernel is the proper place to have this because the kernel knows everything about itself (the mitigations it might have), and the CPU (its model, and microcode features that are exposed). Note however that some vulnerabilities are not reported through this file hierarchy at all, such as Zenbleed.
|
||||
|
||||
However I see a few reasons why this script might still be useful to you, and that's why its development has not halted when the `sysfs` hierarchy came out:
|
||||
|
||||
- A given version of the kernel doesn't have knowledge about the future. To put it in another way: a given version of the kernel only has the understanding of a vulnerability available at the time it was compiled. Let me explain this: when a new vulnerability comes out, new versions of the microcode and kernels are released, with mitigations in place. With such a kernel, a new `sysfs` entry will appear. However, after a few weeks or months, corner cases can be discovered, previously-thought unaffected CPUs can turn out to be affected in the end, and sometimes mitigations can end up being insufficient. Of course, if you're always running the latest kernel version from kernel.org, this issue might be limited for you. The spectre-meltdown-checker script doesn't depend on a kernel's knowledge and understanding of a vulnerability to compute its output. That is, unless you tell it to (using the `--sysfs-only` option).
|
||||
|
||||
- Mitigating a vulnerability completely can sometimes be tricky, and have a lot of complicated prerequisites, depending on your kernel version, CPU vendor, model and even sometimes stepping, CPU microcode, hypervisor support, etc. The script gives a very detailed insight about each of the prerequisites of mitigation for every vulnerability, step by step, hence pointing out what is missing on your system as a whole to completely mitigate an issue.
|
||||
|
||||
- The script can be pointed at a kernel image, and will deep dive into it, telling you if this kernel will mitigate vulnerabilities that might be present on your system. This is a good way to verify before booting a new kernel, that it'll mitigate the vulnerabilities you expect it to, especially if you modified a few config options around these topics.
|
||||
|
||||
- The script will also work regardless of the custom patches that might be integrated in the kernel you're running (or you're pointing it to, in offline mode), and completely ignores the advertised kernel version, to tell whether a given kernel mitigates vulnerabilities. This is especially useful for non-vanilla kernel, where patches might be backported, sometimes silently (this has already happened, too).
|
||||
|
||||
- Educational purposes: the script gives interesting insights about a vulnerability, and how the different parts of the system work together to mitigate it.
|
||||
|
||||
There are probably other reasons, but that are the main ones that come to mind. In the end, of course, only you can tell whether it's useful for your use case ;)
|
||||
|
||||
## How does this script work?
|
||||
|
||||
On one hand, the script gathers information about your CPU, and the features exposed by its microcode. To do this, it uses the low-level CPUID instruction (through the `cpuid` kernel module under Linux, and the `cpucontrol` tool under BSD), and queries to the MSR registers of your CPU (through the `msr` kernel module under Linux, and the `cpucontrol` tool under BSD).
|
||||
|
||||
On another hand, the script looks into the kernel image your system is running on, for clues about the mitigations it supports. Of course, this is very specific for each operating system, even if the implemented mitigation is functionally the same, the actual code is completely specific. As you can imagine, the Linux kernel code has a few in common with a BSD kernel code, for example. Under Linux, the script supports looking into the kernel image, and possibly the System.map and kernel config file, if these are available. Under BSD, it looks into the kernel file only.
|
||||
|
||||
Then, for each vulnerability it knows about, the script decides whether your system is [affected, vulnerable, and mitigated](#what-do-affected-vulnerable-and-mitigated-mean-exactly) against it, using the information it gathered about your hardware and your kernel.
|
||||
|
||||
## Which BSD OSes are supported?
|
||||
|
||||
For the BSD range of operating systems, the script will work as long as the BSD you're using supports `cpuctl` and `linprocfs`. This is not the case for OpenBSD for example. Known BSD flavors having proper support are: FreeBSD, NetBSD, DragonflyBSD. Derivatives of those should also work. To know why other BSDs will likely never be supported, see [why is my OS not supported?](#why-is-my-os-not-supported).
|
||||
|
||||
## Why is my OS not supported?
|
||||
|
||||
This tool only supports Linux, and [some flavors of BSD](#which-bsd-oses-are-supported). Other OSes will most likely never be supported, due to [how this script works](#how-does-this-script-work). It would require implementing these OSes specific way of querying the CPU. It would also require to get documentation (if available) about how this OS mitigates each vulnerability, down to this OS kernel code, and if documentation is not available, reverse-engineer the difference between a known old version of a kernel, and a kernel that mitigates a new vulnerability. This means that all the effort has to be duplicated times the number of supported OSes, as everything is specific, by construction. It also implies having a deep understanding of every OS, which takes years to develop. However, if/when other tools appear for other OSes, that share the same goal of this one, they might be listed here as a convenience.
|
||||
|
||||
## The tool says there is an updated microcode for my CPU, but I don't have it!
|
||||
|
||||
Even if your operating system is fully up to date, the tool might still tell you that there is a more recent microcode version for your CPU. Currently, it uses (and merges) information from 4 sources:
|
||||
|
||||
- The official [Intel microcode repository](https://github.com/intel/Intel-Linux-Processor-Microcode-Data-Files)
|
||||
- The awesome platomav's [MCExtractor database](https://github.com/platomav/MCExtractor) for non-Intel CPUs
|
||||
- The official [linux-firmware](https://git.kernel.org/pub/scm/linux/kernel/git/firmware/linux-firmware.git) repository for AMD
|
||||
- Specific Linux kernel commits that sometimes hardcode microcode versions, such as for [Zenbleed](https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=522b1d69219d8f083173819fde04f994aa051a98) or for the bad [Spectre](https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/tree/arch/x86/kernel/cpu/intel.c#n141) microcodes
|
||||
|
||||
Generally, it means a more recent version of the microcode has been seen in the wild. However, fully public availability of this microcode might be limited yet, or your OS vendor might have chosen not to ship this new version (yet), maybe because it's currently being tested, or for other reasons. This tool can't tell you when or if this will be the case. You should ask your vendor about it. Technically, you can still go and upgrade your microcode yourself, and use this tool to confirm whether you did it successfully. Updating the microcode for you is out of the scope of this tool, as this would violate [rule 1b](#what-are-the-main-design-decisions-regarding-this-script).
|
||||
|
||||
## The tool says that I need a more up-to-date microcode, but I have the more recent version!
|
||||
|
||||
This can happen for a few reasons:
|
||||
|
||||
- Your CPU is no longer supported by the vendor. In that case, new versions of the microcode will never be published, and vulnerabilities requiring microcode features will never be fixed. On most of these vulnerabilities, you'll have no way to mitigate the issue on a vulnerable system, appart from buying a more recent CPU. Sometimes, you might be able to mitigate the issue by disabling a CPU feature instead (often at the cost of speed). When this is the case, the script will list this as one of the possible mitigations for the vulnerability.
|
||||
|
||||
- The vulnerability is recent, and your CPU has not yet received a microcode update for the vendor. Often, these updates come in batches, and it can take several batches to cover all the supported CPUs.
|
||||
|
||||
In both cases, you can contact your vendor to know whether there'll be an update or not, and if yes, when. For Intel, at the time this FAQ entry was written, such guidance was [available here](https://software.intel.com/content/www/us/en/develop/topics/software-security-guidance/processors-affected-consolidated-product-cpu-model.html).
|
||||
|
||||
## Which rules are governing the support of a CVE in this tool?
|
||||
|
||||
On the early days, it was easy: just Spectre and Meltdown (hence the tool name), because that's all we had. Now that this range of vulnerability is seeing a bunch of newcomers every year, this question is legitimate.
|
||||
|
||||
To stick with this tool's goal, a good indication as to why a CVE should be supported, is when mitigating it requires either kernel modifications, microcode modifications, or both.
|
||||
|
||||
Counter-examples include (non-exhaustive list):
|
||||
|
||||
- [CVE-2019-14615](https://github.com/speed47/spectre-meltdown-checker/issues/340), mitigating this issue is done by updating the Intel driver. This is out of the scope of this tool.
|
||||
- [CVE-2019-15902](https://github.com/speed47/spectre-meltdown-checker/issues/304), this CVE is due to a bad backport in the stable kernel. If the faulty backport was part of the mitigation of another supported CVE, and this bad backport was detectable (without hardcoding kernel versions, see [rule 2](#why-are-those-vulnerabilities-so-different-than-regular-cves)), it might have been added as a bullet point in the concerned CVE's section in the tool. However, this wasn't the case.
|
||||
- The "[Take A Way](https://github.com/speed47/spectre-meltdown-checker/issues/344)" vulnerability, AMD said that they believe this is not a new attack, hence there were no microcode and no kernel modification made. As there is nothing to look for, this is out of the scope of this tool.
|
||||
- [CVE-2020-0550](https://github.com/speed47/spectre-meltdown-checker/issues/347), the vendor thinks this is hardly exploitable in the wild, and as mitigations would be too performance impacting, as a whole the industry decided to not address it. As there is nothing to check for, this is out of the scope of this tool.
|
||||
- [CVE-2020-0551](https://github.com/speed47/spectre-meltdown-checker/issues/348), the industry decided to not address it, as it is believed mitigations for other CVEs render this attack practically hard to make, Intel just released an updated SDK for SGX to help mitigate the issue, but this is out of the scope of this tool.
|
||||
|
||||
Look for the [information](https://github.com/speed47/spectre-meltdown-checker/issues?q=is%3Aissue+is%3Aopen+label%3Ainformation) tag in the issues list for more examples.
|
||||
97
README.md
97
README.md
|
|
@ -1,35 +1,53 @@
|
|||
Spectre & Meltdown Checker
|
||||
==========================
|
||||
|
||||
A shell script to tell if your system is vulnerable against the several "speculative execution" CVEs that were made public since 2018.
|
||||
- CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1'
|
||||
- CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2'
|
||||
- CVE-2017-5754 [rogue data cache load] aka 'Meltdown' aka 'Variant 3'
|
||||
- CVE-2018-3640 [rogue system register read] aka 'Variant 3a'
|
||||
- CVE-2018-3639 [speculative store bypass] aka 'Variant 4'
|
||||
- CVE-2018-3615 [L1 terminal fault] aka 'Foreshadow (SGX)'
|
||||
- CVE-2018-3620 [L1 terminal fault] aka 'Foreshadow-NG (OS)'
|
||||
- CVE-2018-3646 [L1 terminal fault] aka 'Foreshadow-NG (VMM)'
|
||||
- CVE-2018-12126 [microarchitectural store buffer data sampling (MSBDS)] aka 'Fallout'
|
||||
- CVE-2018-12130 [microarchitectural fill buffer data sampling (MFBDS)] aka 'ZombieLoad'
|
||||
- CVE-2018-12127 [microarchitectural load port data sampling (MLPDS)] aka 'RIDL'
|
||||
- CVE-2019-11091 [microarchitectural data sampling uncacheable memory (MDSUM)] aka 'RIDL'
|
||||
- CVE-2019-11135 [TSX asynchronous abort] aka 'TAA' aka 'ZombieLoad V2'
|
||||
- CVE-2018-12207 [machine check exception on page size changes (MCEPSC)] aka 'No eXcuses' aka 'iTLB Multihit'
|
||||
A shell script to assess your system's resilience against the several [transient execution](https://en.wikipedia.org/wiki/Transient_execution_CPU_vulnerability) CVEs that were published since early 2018, and give you guidance as to how to mitigate them.
|
||||
|
||||
CVE | Name | Aliases
|
||||
------------------------------------------------------------------------------- | --------------------------------------------------- | ---------------------------------
|
||||
[CVE-2017-5753](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5754) | Bounds Check Bypass | Spectre Variant 1
|
||||
[CVE-2017-5715](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5715) | Branch Target Injection | Spectre Variant 2
|
||||
[CVE-2017-5754](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-5754) | Rogue Data Cache Load | Meltdown, Variant 3
|
||||
[CVE-2018-3640](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-3640) | Rogue System Register Read | Variant 3a
|
||||
[CVE-2018-3639](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-3639) | Speculative Store Bypass | Variant 4
|
||||
[CVE-2018-3615](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-3615) | L1 Terminal Fault | L1TF, Foreshadow (SGX)
|
||||
[CVE-2018-3620](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-3620) | L1 Terminal Fault | L1TF, Foreshadow-NG (OS)
|
||||
[CVE-2018-3646](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-3646) | L1 Terminal Fault | L1TF, Foreshadow-NG (VMM)
|
||||
[CVE-2018-12126](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12126) | Microarchitectural Store Buffer Data Sampling | MSBDS, Fallout
|
||||
[CVE-2018-12130](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12130) | Microarchitectural Fill Buffer Data Sampling | MFBDS, ZombieLoad
|
||||
[CVE-2018-12127](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12127) | Microarchitectural Load Port Data Sampling | MLPDS, RIDL
|
||||
[CVE-2019-11091](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11091) | Microarchitectural Data Sampling Uncacheable Memory | MDSUM, RIDL
|
||||
[CVE-2019-11135](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11135) | TSX asynchronous abort | TAA, ZombieLoad V2
|
||||
[CVE-2018-12207](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12207) | Machine Check Exception on Page Size Changes | MCEPSC, No eXcuses, iTLB Multihit
|
||||
[CVE-2020-0543](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-0543) | Special Register Buffer Data Sampling | SRBDS
|
||||
[CVE-2022-40982](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-40982) | Gather Data Sampling | GDS, Downfall
|
||||
[CVE-2023-20569](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-20569) | Return Address Security | Inception, RAS, SRSO
|
||||
[CVE-2023-20593](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-20593) | Cross-Process Information Leak | Zenbleed
|
||||
[CVE-2023-23583](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-23583) | Redundant Prefix issue | Reptar
|
||||
|
||||
Supported operating systems:
|
||||
- Linux (all versions, flavors and distros)
|
||||
- BSD (FreeBSD, NetBSD, DragonFlyBSD)
|
||||
- FreeBSD, NetBSD, DragonFlyBSD and derivatives (others BSDs are [not supported](FAQ.md#which-bsd-oses-are-supported))
|
||||
|
||||
For Linux systems, the tool will detect mitigations, including backported non-vanilla patches, regardless of the advertised kernel version number and the distribution (such as Debian, Ubuntu, CentOS, RHEL, Fedora, openSUSE, Arch, ...), it also works if you've compiled your own kernel. More information [here](FAQ.md#how-does-this-script-work).
|
||||
|
||||
Other operating systems such as MacOS, Windows, ESXi, etc. [will most likely never be supported](FAQ.md#why-is-my-os-not-supported).
|
||||
|
||||
Supported architectures:
|
||||
- x86 (32 bits)
|
||||
- amd64/x86_64 (64 bits)
|
||||
- ARM and ARM64
|
||||
- `x86` (32 bits)
|
||||
- `amd64`/`x86_64` (64 bits)
|
||||
- `ARM` and `ARM64`
|
||||
- other architectures will work, but mitigations (if they exist) might not always be detected
|
||||
|
||||
For Linux systems, the script will detect mitigations, including backported non-vanilla patches, regardless of the advertised kernel version number and the distribution (such as Debian, Ubuntu, CentOS, RHEL, Fedora, openSUSE, Arch, ...), it also works if you've compiled your own kernel.
|
||||
## Frequently Asked Questions (FAQ)
|
||||
|
||||
For BSD systems, the detection will work as long as the BSD you're using supports `cpuctl` and `linprocfs` (this is not the case of OpenBSD for example).
|
||||
- What is the purpose of this tool?
|
||||
- Why was it written?
|
||||
- How can it be useful to me?
|
||||
- How does it work?
|
||||
- What can I expect from it?
|
||||
|
||||
All these questions (and more) have detailed answers in the [FAQ](FAQ.md), please have a look!
|
||||
|
||||
## Easy way to run the script
|
||||
|
||||
|
|
@ -73,15 +91,15 @@ docker run --rm --privileged -v /boot:/boot:ro -v /dev/cpu:/dev/cpu:ro -v /lib/m
|
|||
|
||||
- Intel Haswell CPU running under Ubuntu 16.04 LTS
|
||||
|
||||

|
||||

|
||||
|
||||
- AMD Ryzen running under OpenSUSE Tumbleweed
|
||||
|
||||

|
||||
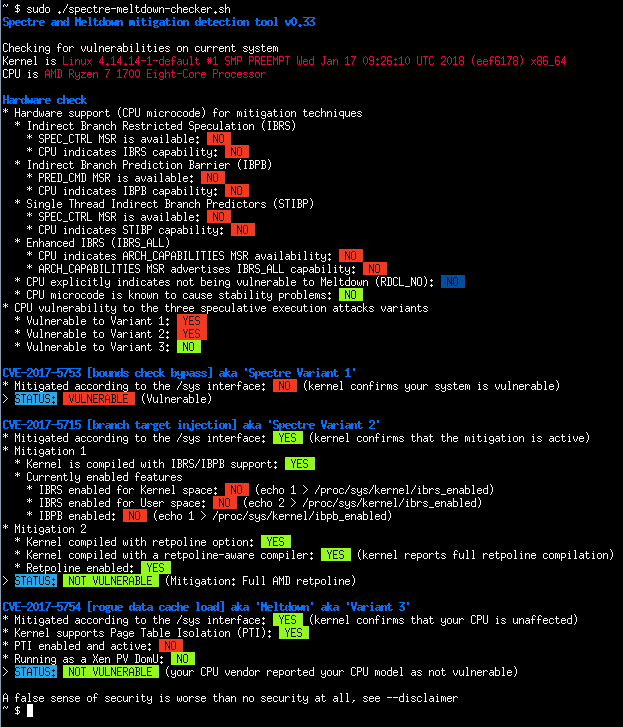
|
||||
|
||||
- Batch mode (JSON flavor)
|
||||
|
||||

|
||||

|
||||
|
||||
## Quick summary of the CVEs
|
||||
|
||||
|
|
@ -159,15 +177,32 @@ docker run --rm --privileged -v /boot:/boot:ro -v /dev/cpu:/dev/cpu:ro -v /lib/m
|
|||
- Mitigation: disable hugepages use in hypervisor, or update hypervisor to benefit from mitigation
|
||||
- Performance impact of the mitigation: low to significant
|
||||
|
||||
## Understanding what this script does and doesn't
|
||||
**CVE-2020-0543** Special Register Buffer Data Sampling (SRBDS)
|
||||
|
||||
This tool does its best to determine whether your system is immune (or has proper mitigations in place) for the collectively named "speculative execution" vulnerabilities. It doesn't attempt to run any kind of exploit, and can't guarantee that your system is secure, but rather helps you verifying whether your system has the known correct mitigations in place.
|
||||
However, some mitigations could also exist in your kernel that this script doesn't know (yet) how to detect, or it might falsely detect mitigations that in the end don't work as expected (for example, on backported or modified kernels).
|
||||
- Impact: Kernel
|
||||
- Mitigation: microcode update + kernel update helping to protect various CPU internal buffers from unprivileged speculative access to data
|
||||
- Performance impact of the mitigation: low
|
||||
|
||||
Your system exposure also depends on your CPU. As of now, AMD and ARM processors are marked as immune to some or all of these vulnerabilities (except some specific ARM models). All Intel processors manufactured since circa 1995 are thought to be vulnerable, except some specific/old models, such as some early Atoms. Whatever processor one uses, one might seek more information from the manufacturer of that processor and/or of the device in which it runs.
|
||||
**CVE-2022-40982** Gather Data Sampling (GDS, Downfall)
|
||||
|
||||
The nature of the discovered vulnerabilities being quite new, the landscape of vulnerable processors can be expected to change over time, which is why this script makes the assumption that all CPUs are vulnerable, except if the manufacturer explicitly stated otherwise in a verifiable public announcement.
|
||||
- Impact: Kernel & all software
|
||||
- Mitigation: either microcode update or disabling AVX feature
|
||||
- Performance impact of the mitigation: TBD
|
||||
|
||||
Please also note that for Spectre vulnerabilities, all software can possibly be exploited, this tool only verifies that the kernel (which is the core of the system) you're using has the proper protections in place. Verifying all the other software is out of the scope of this tool. As a general measure, ensure you always have the most up to date stable versions of all the software you use, especially for those who are exposed to the world, such as network daemons and browsers.
|
||||
**CVE-2023-20569** Return Address Security (Inception)
|
||||
|
||||
This tool has been released in the hope that it'll be useful, but don't use it to jump to conclusions about your security.
|
||||
- Impact: Kernel & all software
|
||||
- Mitigation: updated kernel & microcode
|
||||
- Performance impact of the mitigation: low to significant depending on the mitigation
|
||||
|
||||
**CVE-2023-20593** Cross-Process Information Leak (Zenbleed)
|
||||
|
||||
- Impact: Kernel & all software
|
||||
- Mitigation: either kernel mitigation by disabling a CPU optimization through an MSR bit, or CPU microcode mitigation
|
||||
- Performance impact of the mitigation: TBD
|
||||
|
||||
**CVE-2023-23583** Redundant Prefix issue (Reptar)
|
||||
|
||||
- Impact: All software
|
||||
- Mitigation: microcode update for the affected CPU
|
||||
- Performance impact of the mitigation: low
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load Diff
Loading…
Reference in New Issue